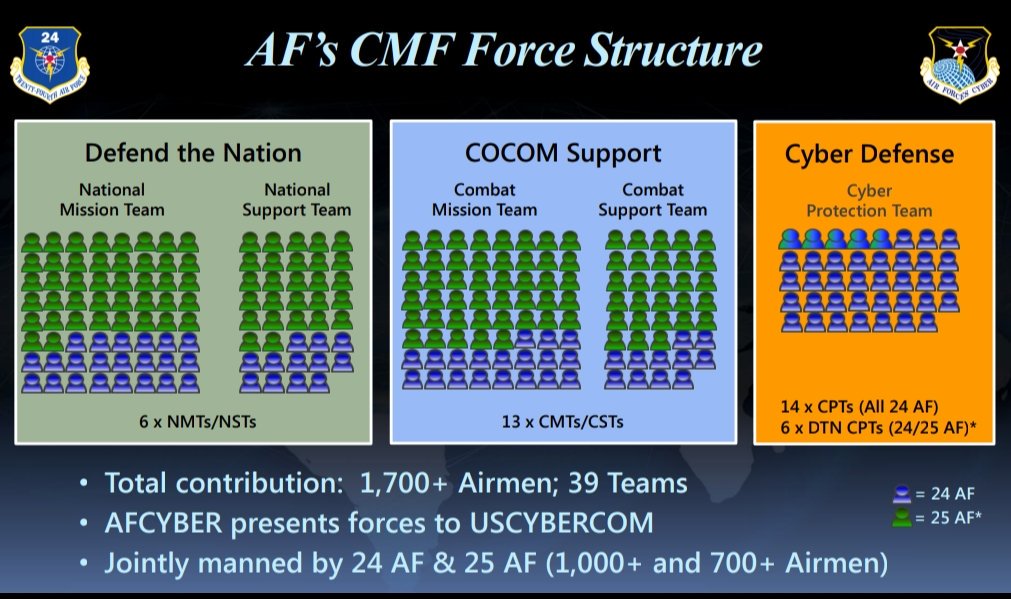
Cyber Protection Team Structure
Cdn Ymaws Com Www Alamoafcea Org Resource Resmgr Lunch Speakers Doc Delange Eric Pdf
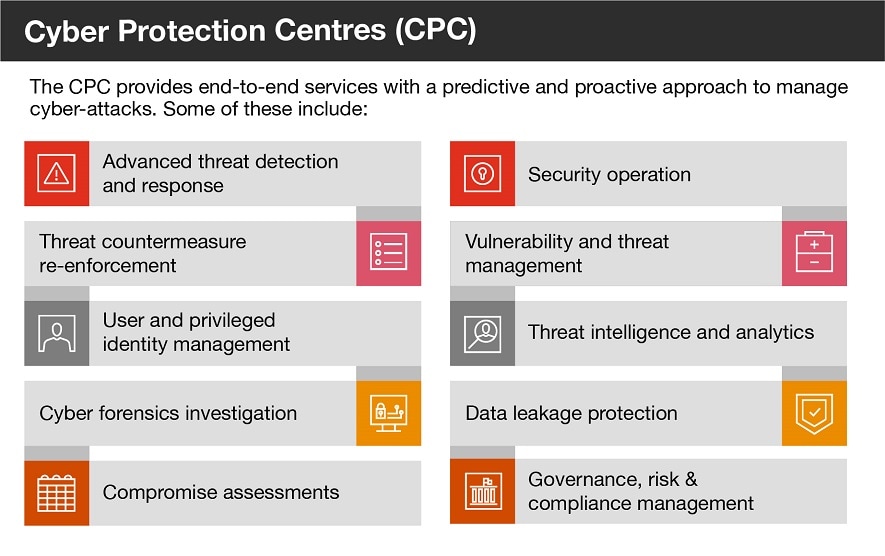
Cyber Protection Centre

Creating And Implementing An Effective And Deterrent National Cyber Security Strategy
Cyber Protection Team Structure のギャラリー
Structure And Organisation Enisa
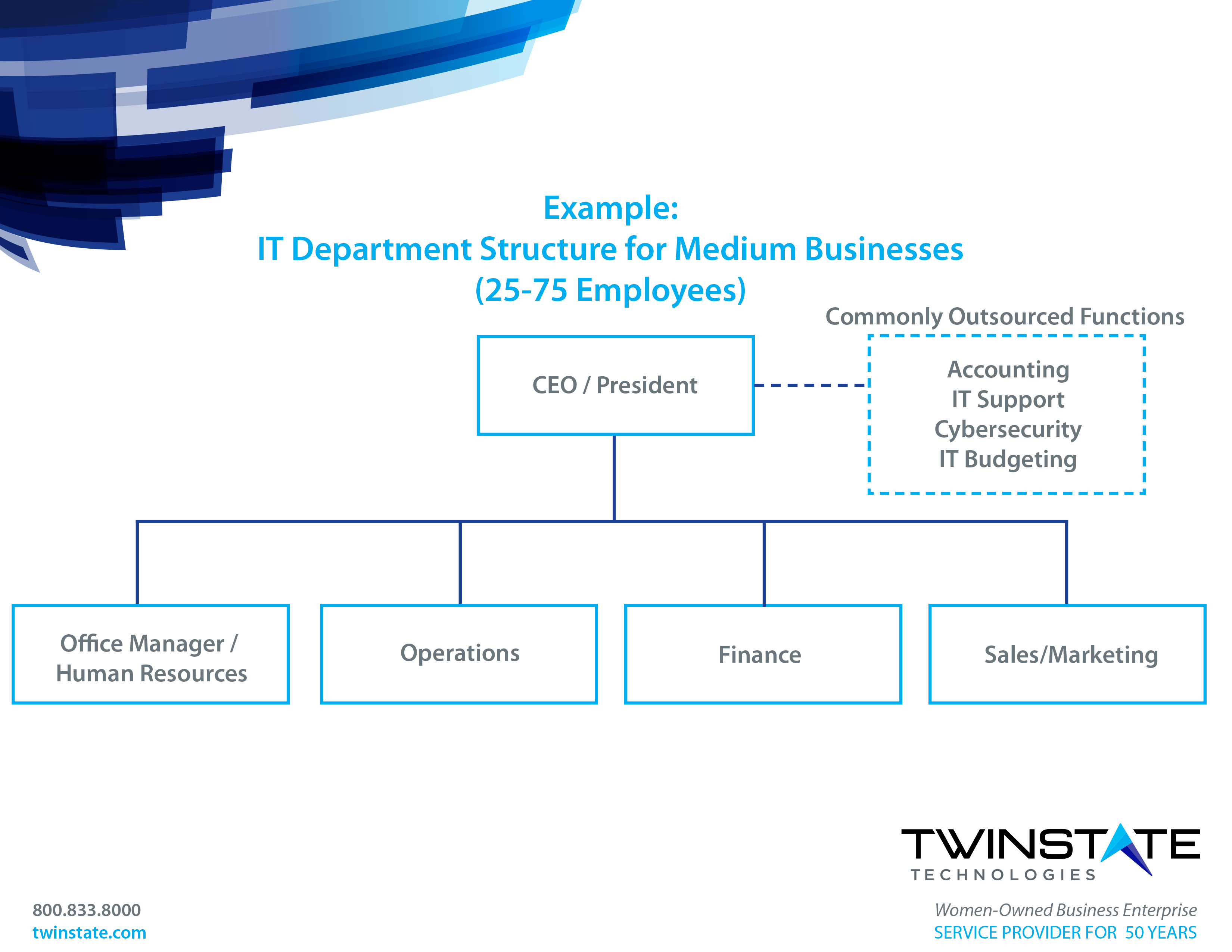
It Department Structure Tips And Best Practices
/arc-anglerfish-arc2-prod-mco.s3.amazonaws.com/public/QXVUVNU47FEQXKH5W6XO7REAIA.jpg)
A Peek Inside Army Cyber Protection Teams
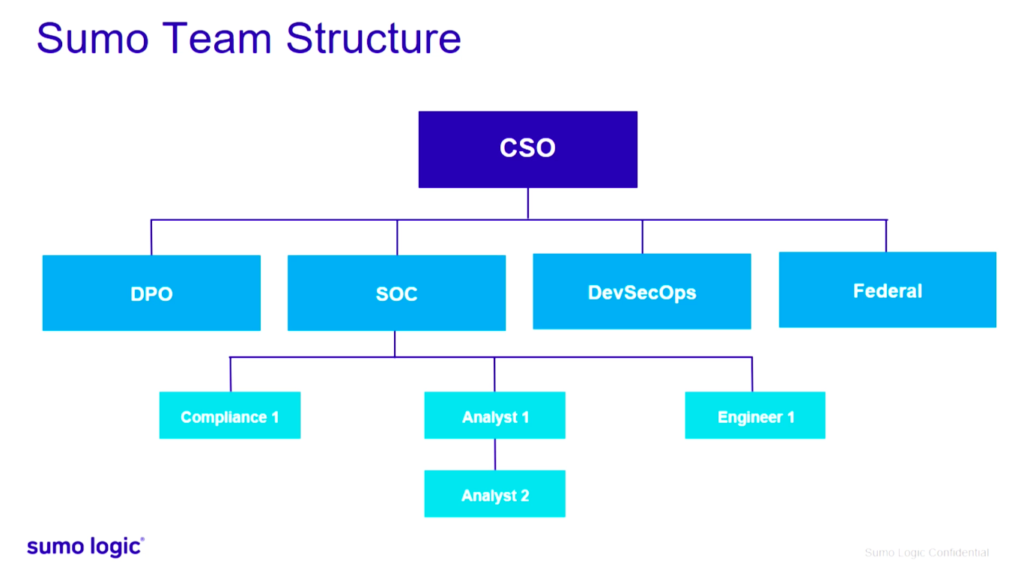
Pokemon Co International And Sumo Logic S Joint Journey To Build A Modern Day Soc Sumo Logic

Co National Guard Army Cyber

A New Posture For Cybersecurity In A Networked World Mckinsey
Apps Dtic Mil Dtic Tr Fulltext U2 Pdf
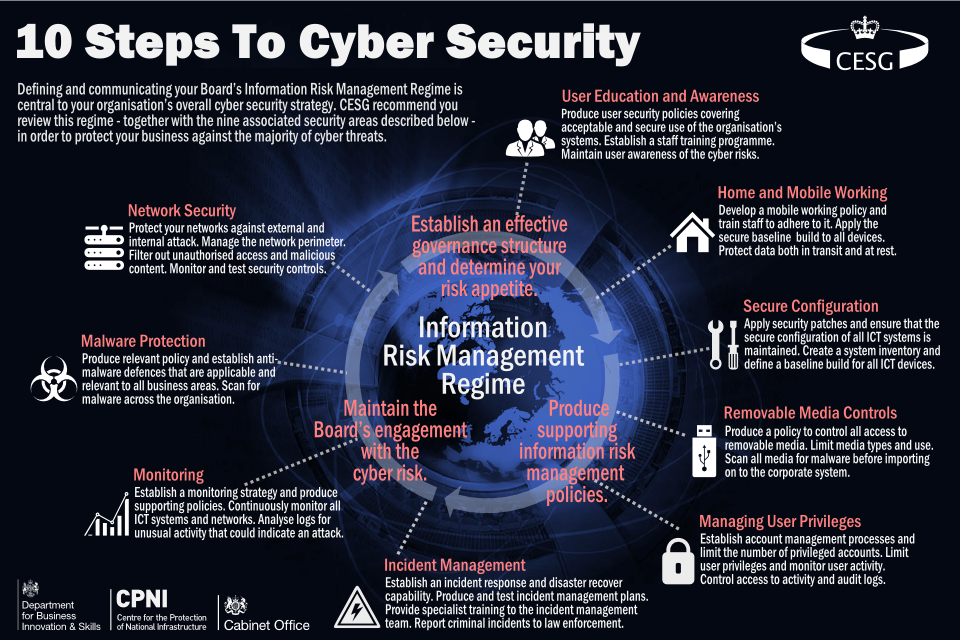
Withdrawn 10 Steps Summary Gov Uk
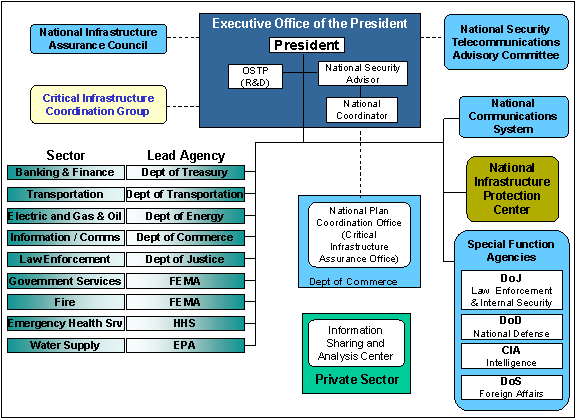
The Department Of Defense Critical Infrastructure Protection Cip Plan Version 1 0
Www Itu Int Dms Pub Itu D Opb Str D Str Gci 01 18 Pdf E Pdf

Creating And Implementing An Effective And Deterrent National Cyber Security Strategy

U S Marine Corps Concepts Programs Organization Operating Forces U S Marine Corps Forces Cyberspace Command
Generali Group
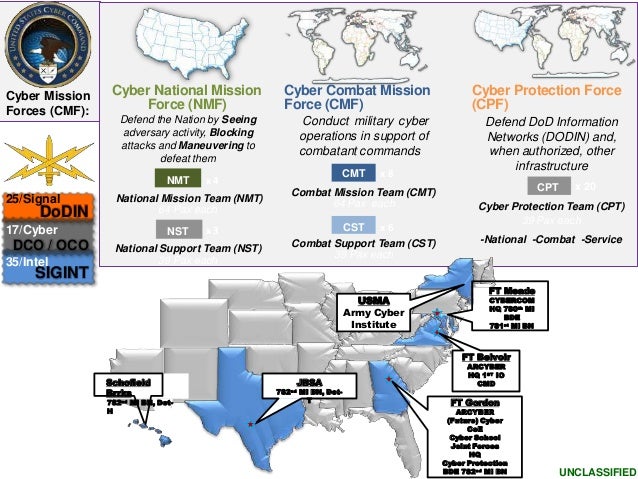
Office Chief Of Cyber Personnel Presentation Technet Augusta 15

National Cyber Security Division Wikipedia

United States Army Cyber Command Wikipedia
Www Gao Gov Assets 700 Pdf

Cyber Protection Team Tools Supporting Cyber Protection Teams Cpt Redseal
Apps Dtic Mil Dtic Tr Fulltext U2 Pdf
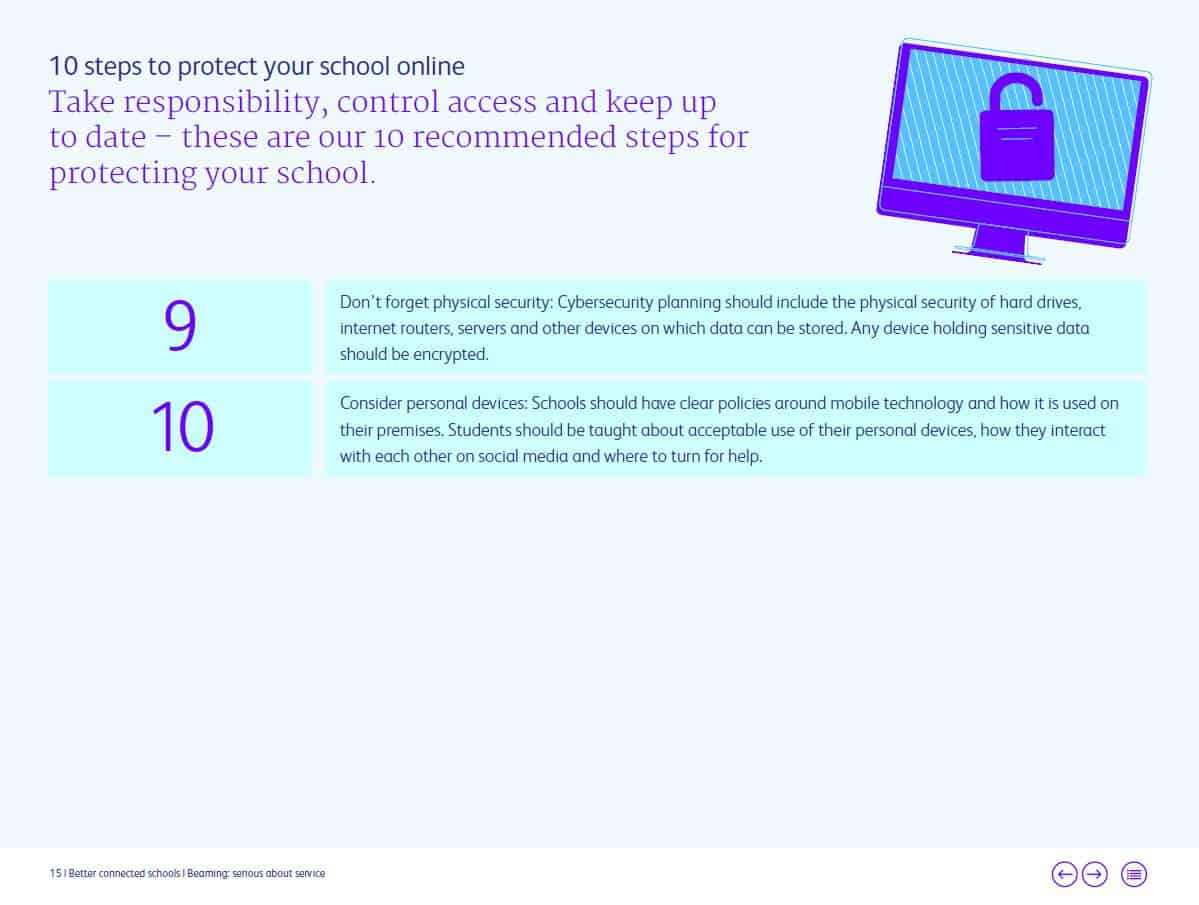
Cybersecurity Safeguarding For Schools What You Need To Know About Threats Online

Creating And Implementing An Effective And Deterrent National Cyber Security Strategy

Cybersecurity Reference Architecture Security For A Hybrid Enterprise Microsoft Security

Building The Right Cyber Security Team Structure Stickman
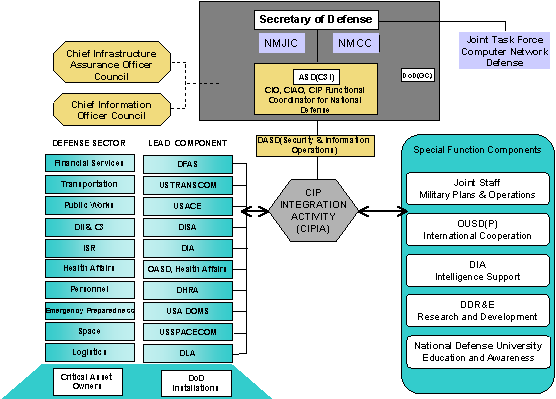
The Department Of Defense Critical Infrastructure Protection Cip Plan Version 1 0

Cyber Mission Force Achieves Full Operational Capability U S Department Of Defense Defense Department News
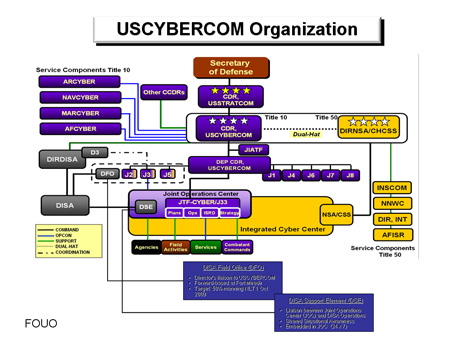
United States Cyber Command Uscybercom Schema Root News

Twncert 國家電腦事件處理中心
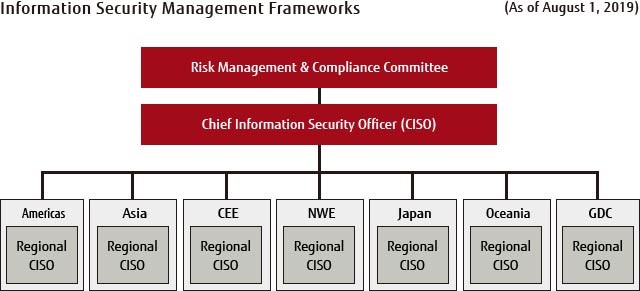
Information Security Fujitsu Global

Upending Tradition Modeling Tomorrow S Cybersecurity Organization Heidrick Struggles

Organizational Structure Ministry Of Transport And Communications

Cyber Security Framework Cpa Global

Cyber Mission Force Achieves Full Operational Capability U S Department Of Defense Defense Department News

Structuring The Chief Information Security Officer Ciso Organization
Q Tbn And9gcrozper4xxevz4 aahb 8oqqu1cy2i44vztzjiahvvoeo0jsc Usqp Cau

Operational Graphics For Cyberspace National Defense University Press Joint Force Quarterly
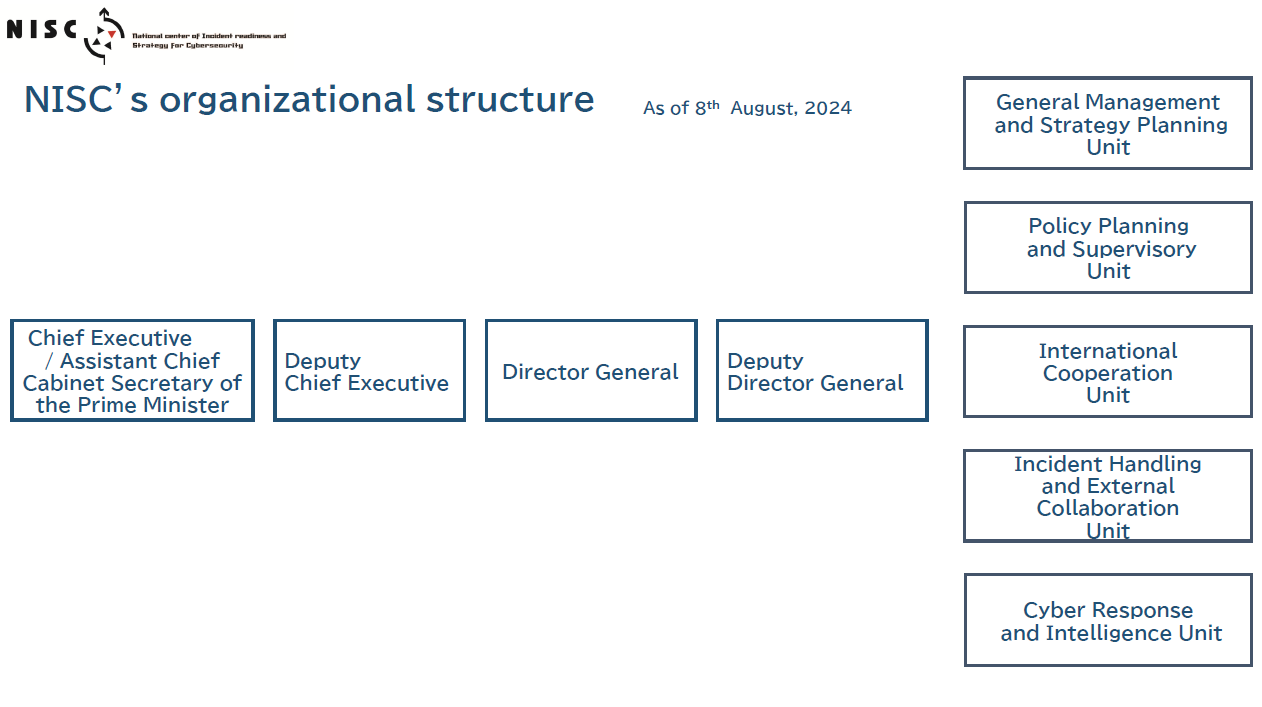
National Center Of Incident Readiness And Strategy For Cybersecurity Nisc

Us National Cybersecurity And Communications Integration Center 19 Download Scientific Diagram
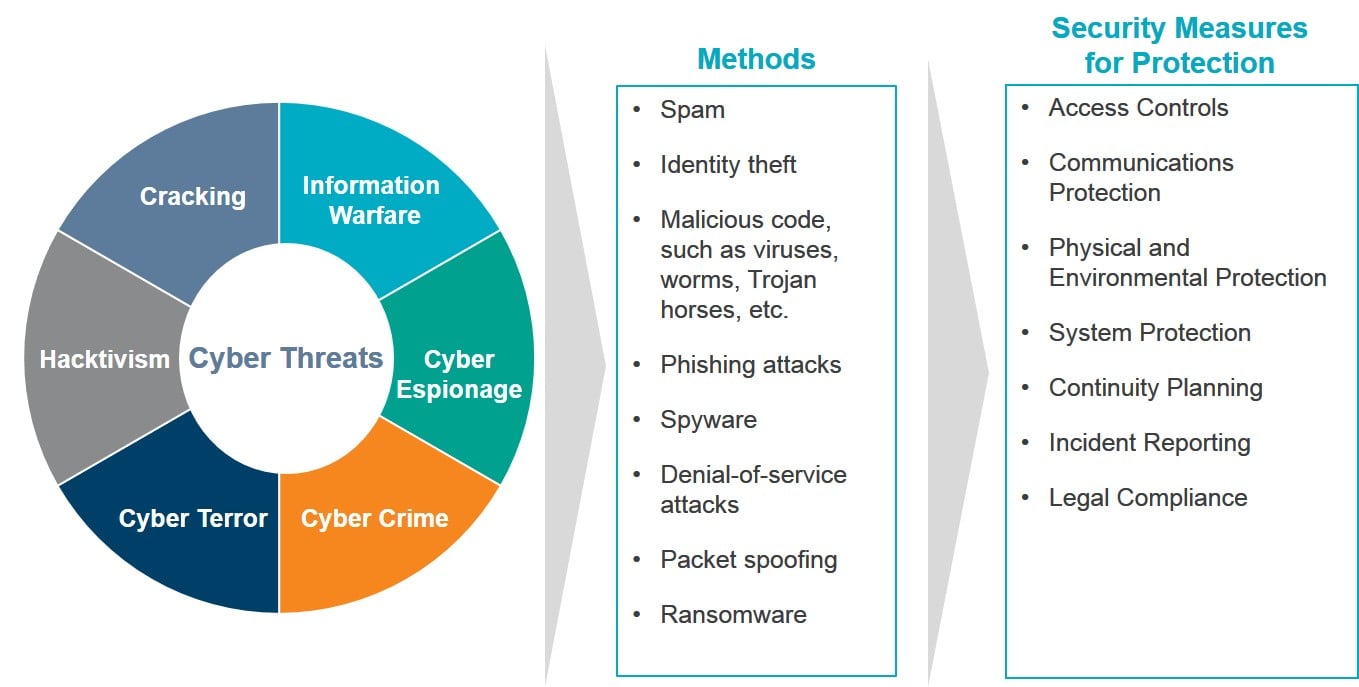
What Is Internal Audit S Role In Cyber Security
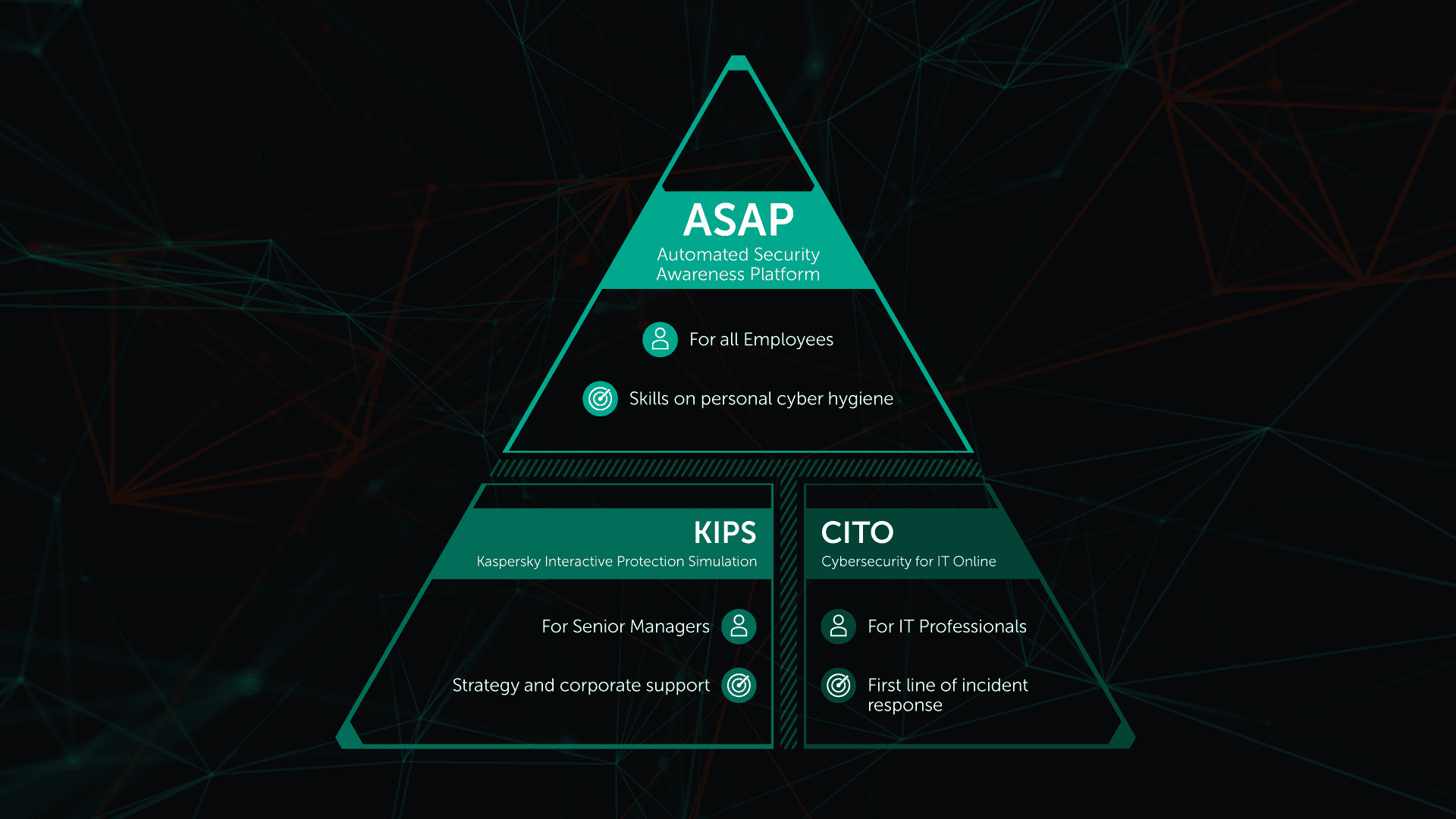
Kaspersky Security Awareness Training Kaspersky
Make Cybersecurity A Strategic Asset
Challenges To Tactical Cyber Defense By Adam Tyra

Roles Of Three Lines Of Defense For Information Security And Governance

Co National Guard Army Cyber

Roles Of Three Lines Of Defense For Information Security And Governance

Afcea State Of Combat Comm Advancing Warfighter Capabilities In Through And From Cyberspace Ppt Video Online Download
Css Ethz Ch Content Dam Ethz Special Interest Gess Cis Center For Securities Studies Pdfs Cyber Reports 08 Japans National Cybersecurity Defense Posture Pdf
Apps Dtic Mil Dtic Tr Fulltext U2 Pdf

Cyber Protection Team Tools Supporting Cyber Protection Teams Cpt Redseal

A New Posture For Cybersecurity In A Networked World Mckinsey
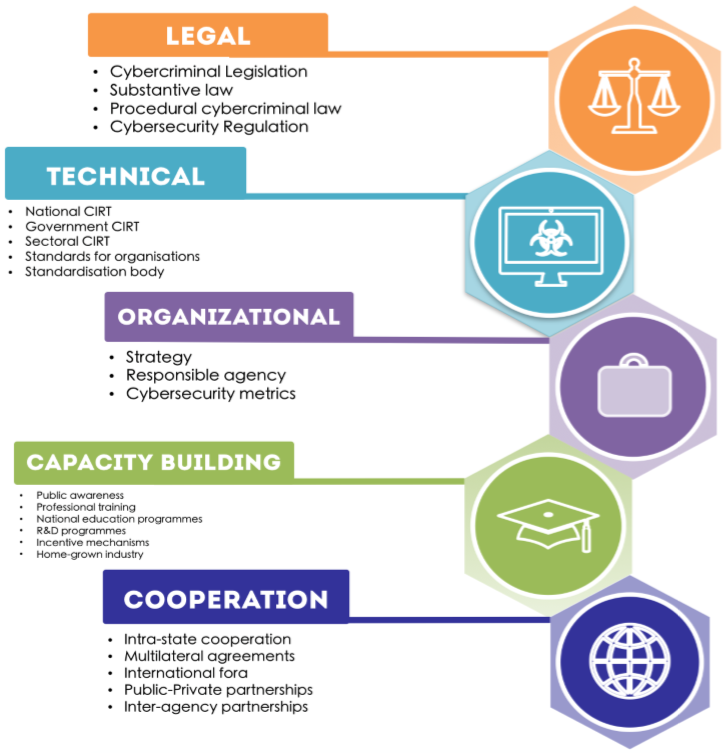
Cybercrime Module 8 Key Issues International Cooperation On Cybersecurity Matters
/cloudfront-us-east-1.images.arcpublishing.com/mco/U4LCRND2SFGPPNC7S4VW2LOVLY.JPG)
The Us Air Force Is Using A New Cyber Training Platform To Evolve Defensive Teams
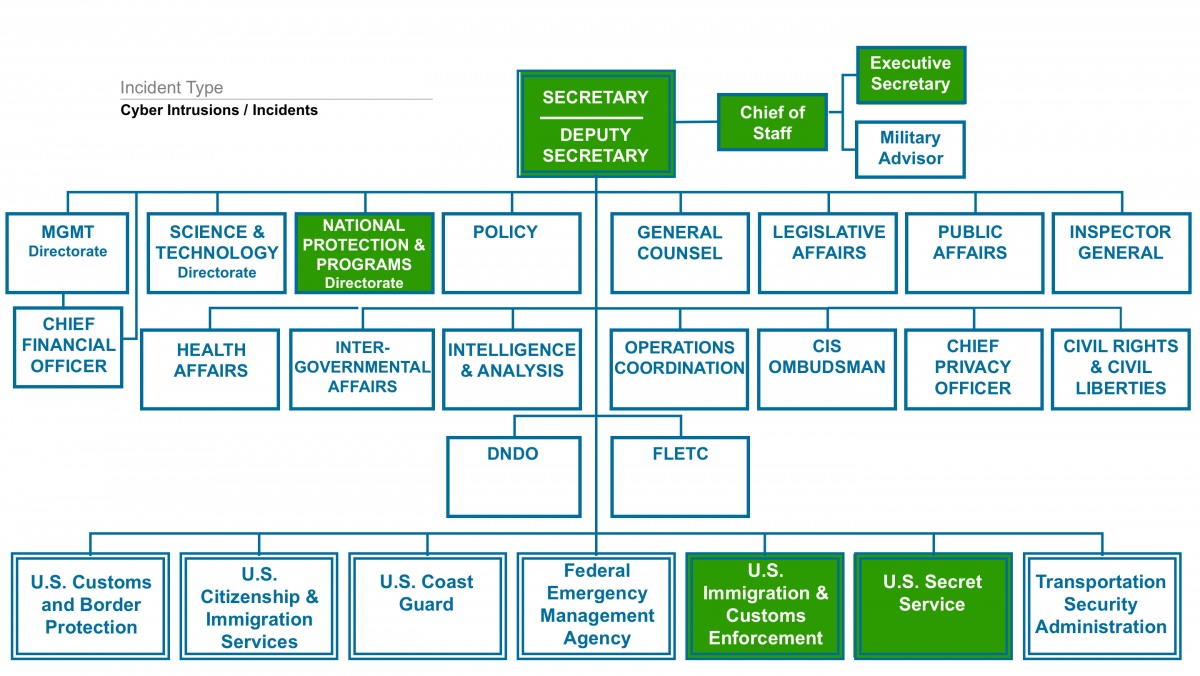
What Dhs Does During A Cyber Attack Homeland Security

Operational Graphics For Cyberspace National Defense University Press Joint Force Quarterly
Rfpb Defense Gov Portals 67 Documents Reports Rfpb Cyber Report Web Pdf

U S Cyber Commands Launches 13 New Cyber Protection Teams
Stefan Soesanto
Www Itu Int En Itu D Cybersecurity Documents National Strategies Repository Mauritius 14 National cyber security strategy 14 en Pdf
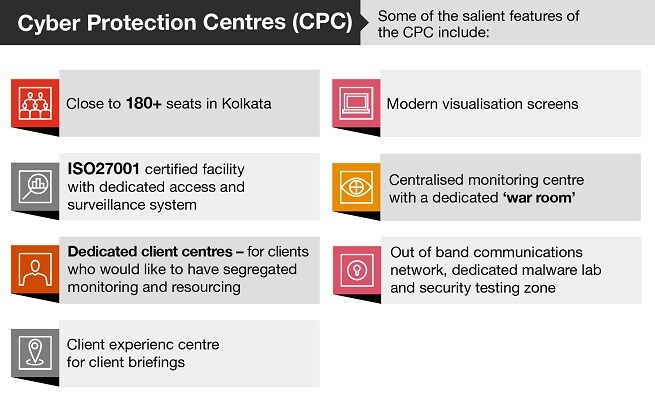
Cyber Protection Centre
What Are Cyber Threats And What To Do About Them The Missing Report
Www Gao Gov Assets 700 Pdf
Q Tbn And9gcqywjbpvc8nagdi1d Tq4khurji6m6qj1kj Rxpjrhwk8g8zq7h Usqp Cau
Archive Defense Gov Home Features 15 0415 Cyber Strategy Final 15 Dod Cyber Strategy For Web Pdf
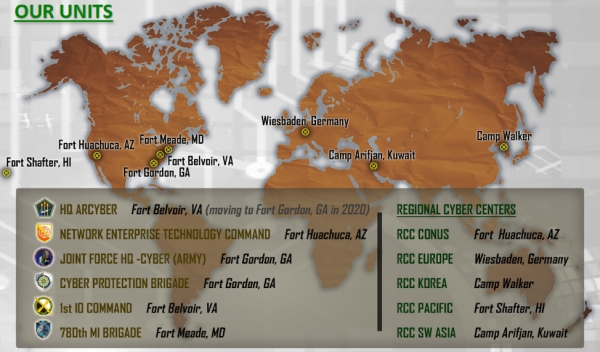
About Army Cyber Command Goarmy Com

Upending Tradition Modeling Tomorrow S Cybersecurity Organization Heidrick Struggles

Upending Tradition Modeling Tomorrow S Cybersecurity Organization Heidrick Struggles

Us National Cybersecurity And Communications Integration Center 19 Download Scientific Diagram
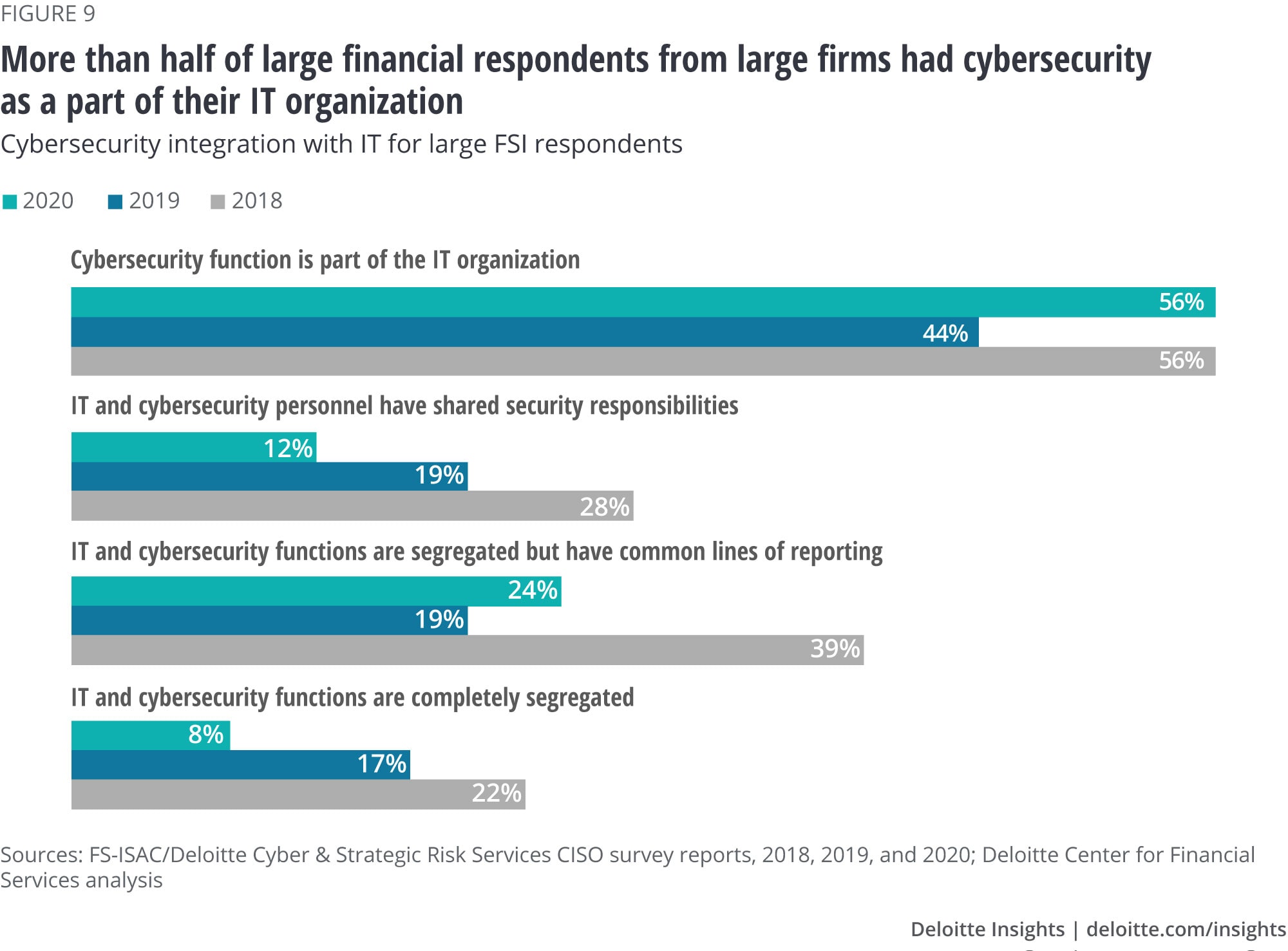
Reshaping The Cybersecurity Landscape Deloitte Insights
/arc-anglerfish-arc2-prod-mco.s3.amazonaws.com/public/WCDAW2PLRREIREINHR4V2DWJ4A.jpg)
Here S How Dod Organizes Its Cyber Warriors
Www Gao Gov Assets 690 Pdf
Q Tbn And9gcqxnpoejhk8fbhvyjxqsparlhgaq1k7tjqv8jouaj9mq0dfy4lj Usqp Cau
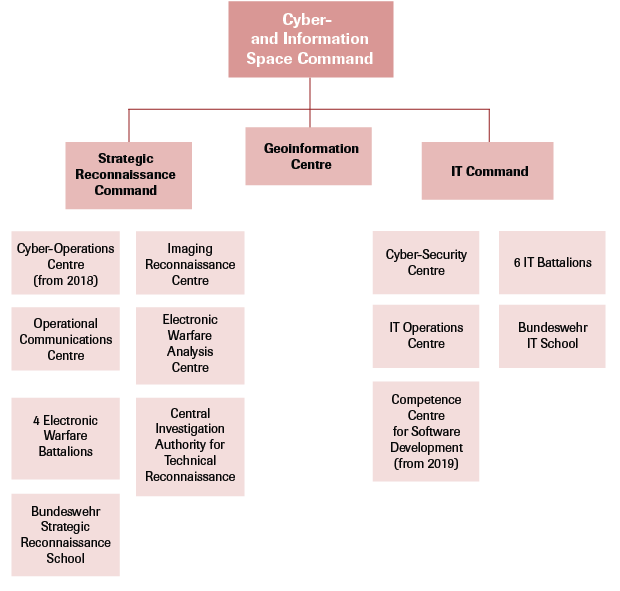
The Cyber And Information Space A New Formation In The Bundeswehr
Http Www Iiroc Ca Industry Documents Cybersecuritybestpracticesguide En Pdf

Command History
Www Itu Int Dms Pub Itu D Opb Str D Str Gci 01 18 Pdf E Pdf

7 Cybersecurity Trends For
Www Nebraskacert Org Csf Csf Aug16 Pdf

Operational Graphics For Cyberspace National Defense University Press Joint Force Quarterly

Afcea State Of Combat Comm Advancing Warfighter Capabilities In Through And From Cyberspace Ppt Video Online Download
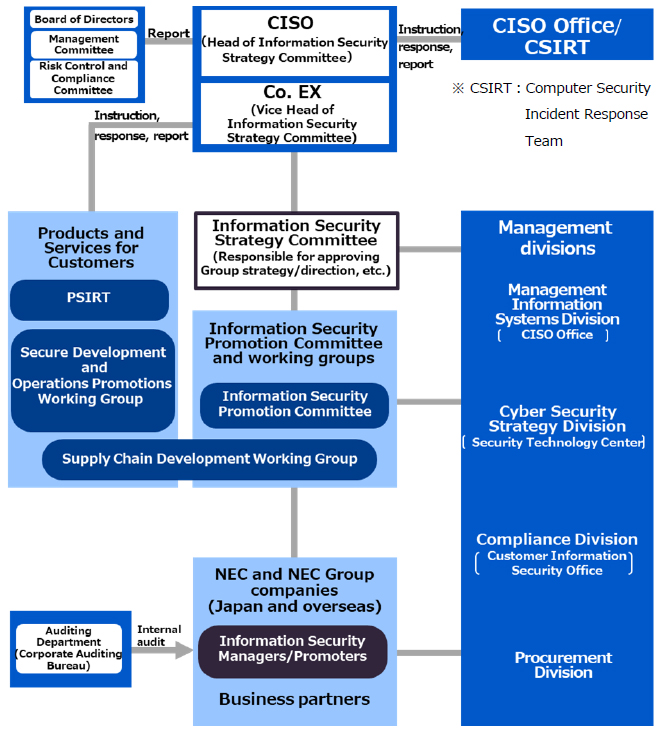
Information Security And Cyber Security Social Nec

Command History
Nicst Ey Gov Tw File 3bf304d39ea

Command History
Dod Fact Sheet Cyber Mission Force U S Army Cyber Command Fact Sheets

Using A Cybersecurity Framework For Web Application Security Netsparker

Co National Guard Army Cyber
Www Gao Gov Assets 700 Pdf
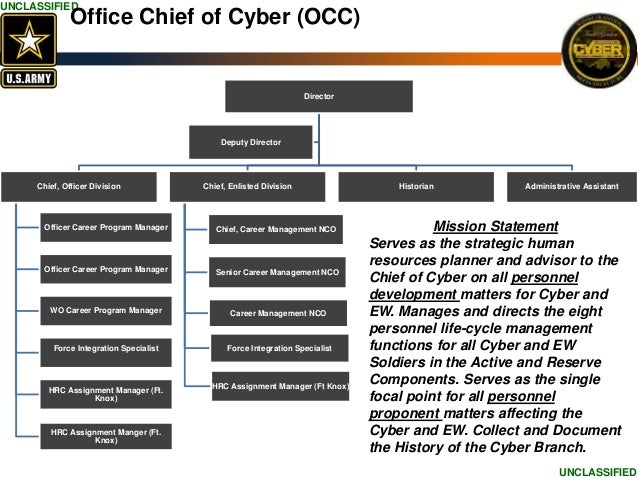
Office Chief Of Cyber Personnel Presentation Technet Augusta 15
Www Jstor Org Stable

Upending Tradition Modeling Tomorrow S Cybersecurity Organization Heidrick Struggles

A New Posture For Cybersecurity In A Networked World Mckinsey

12 Best Cybersecurity Practices In Ekran System
How You Can Comply With The Nist Cybersecurity Framework

Information Security Roles Responsibilities Team Organizational Structure

The Three Pillar Approach To Cyber Security Data And Information Protection Dnv Gl
Www Nga Org Wp Content Uploads 19 04 Issuebrief Mg Pdf
Www Nebraskacert Org Csf Csf Aug16 Pdf

Cybersecurity Architecture Part 2 System Boundary And Boundary Protection

Reshaping The Cybersecurity Landscape Deloitte Insights
Q Tbn And9gct7o9zndl Zjoir7iw0qubkkhxvucz Wix4abymew0rybujkvtd Usqp Cau
Cybersecurity Powerpoint Presentation Slides Powerpoint Presentation Slides Ppt Slides Graphics Sample Ppt Files Template Slide

How To Protect The Physical Security Of The Organization Analytics Insight



